|
FACTS AND APPLICATIONS OF GSM/GPRS MODEM
The GSM/GPRS Modem comes with a serial interface through
which the modem can be controlled using AT command
interface. An antenna and a power adapter are provided.
The basic segregation of working of the modem is as under:
� Voice calls
� SMS
� GSM Data calls
� GPRS
Voice calls: Voice calls are not an application
area to be targeted. In future if interfaces like a
microphone and speaker are provided for some applications
then this can be considered.
SMS: SMS is an area where the modem can be used to
provide features like:
� Pre-stored SMS transmission
� These SMS can be transmitted on certain trigger events
in an automation system
� SMS can also be used in areas where small text
information has to be sent. The transmitter can be an
automation system or machines like vending machines,
collection machines or applications like positioning
systems where the navigator keeps on sending SMS at
particular time intervals
� SMS can be a solution where GSM data call or GPRS
services are not available
GSM Data Calls: Data calls can be made using this
modem. Data calls can be made to a normal PSTN modem/phone
line also (even received). Data calls are basically made
to send/receive data streams between two units either PC�s
or embedded devices. The advantage of Data calls over SMS
is that both parties are capable of sending/receiving data
through their terminals.
Some points to be remembered in case of data calls:
� The data call service doesn�t come with a normal SIM
which is purchased but has to be requested with the
service provider (say Airtel).
� Upon activation of data/fax service you are provided
with two separate numbers i.e. the Data call number and
the Fax service number.
� Data calls are established using Circuit Switched data
connections.
� Right now the speed at which data can be transmitted is
9.6 kbps.
� The modem supports speeds up to 14.4 kbps but the
provider give a maximum data rate of 9.6 kbps during GSM
data call.
� Technologies like HSCSD (high Speed Circuit Switched
Data) will improve drastically the data rates, but still
in pipeline.
Applications And Facts About GSM Data Calls:
� Devices that have communication on serial port either on
PC or in the embedded environment
� Devices that want to communicate with a remote server
for data transfer
� This capability of data transfer can help in reducing
processing requirements of the device
� The basic aim is to provide a wireless solution keeping
the existing firmware intact
� The clients firmware continues to work without any
modifications (no changes in the existing software
required)
� GSM data calls can be a good solution where data has to
be transmitted from a hand-held device to a central server
� The interface on two sides can be between PC�s as well
as embedded devices
� Calls can be established
by the terminals at either side to start data calls
� The Modem remains transparent during data transfer after
the call is established.
� Call establishment utility to be provided in case PC
terminals
� Call establishment to be automated in case of embedded
terminals. GSM converter can be an option where
intelligence of establishing calls has to be put in case
of embedded devices. Concept of GSM converter is discussed
later in this document
Dial-Up Networks Using GSM Data Calls: Dial up
networking is a utility available with Windows through a
person can dial the Data call number of this modem from
any PC and share the file system on either PC�s. This can
be a good utility where both terminals are PC based.
Sharing the file system remotely enables monitoring of
devices remotely. Thus the modem can act as a piece of
device which acts as a spy in the system. Can be a good
debugging utility wherein a person can configure/monitor a
remote PC based system and even rectify it. Some companies
do sell their products with a GSM modem inside it just for
this handy feature which allows them to configure the
machines sitting anywhere in the world. Since the
connection can have upper layer protocols like TCP/IP in
this connection it becomes more reliable and useful.
GSM Converter: GSM converter will be an add-on
device to be attached between a terminal which wants data
transfer and the GSM modem. This GSM converter will take
care of call establishment where the embedded device
cannot make a call. The converter will remain transparent
through-out the call once call is established. The GSM
converter will be a very small piece of hardware possibly
embedded inside the cable itself.
GPRS: This modem can be used to make a GPRS
connection. Upon connection the modem can be used for
internet connectivity of devices.
Key-Points in GPRS:
� The PC/Embedded device dials the Service Provider (say
Airtel)
� Data is routed through the ISP (Internet Service
Provider)
� GPRS is basically Packet Oriented service
� Protocols like TCP/IP are inherent characteristics in
GPRS
� One has to talk in terms of IP addresses here not phone
numbers
� The implementation is more useful where PC�s want to
communicate over GPRS
� Although data transfer is done from embedded devices too
but with reduced features
� Since you are charged either on monthly flat rates or
amount of data transfer taking place GPRS is anyday a
cheaper option as compared to GSM data call. But GPRS
services are not available everywhere.
� The data rate rates in GPRS can go upto 40 kbps
Application areas in GPRS using this Modem:
� Applications where mobile devices want to upload data to
a central server
� Monitoring devices that are continuously logged on to
the server. Since you are charged for the amount of data
transfer hence a continuous connection can be maintained.
� Virtual private networks
� Radius servers
Virtual private networks
A virtual private network (VPN) is the extension of a
private network that encompasses links across shared or
public networks like the Internet. A VPN enables you to
send data between two computers across a shared or public
internetwork in a manner that emulates the properties of a
point-to-point private link. The act of configuring and
creating a virtual private network is known as virtual
private networking.
To emulate a point-to-point link, data is encapsulated, or
wrapped, with a header that provides routing information
allowing it to traverse the shared or public transit
internetwork to reach its endpoint. To emulate a private
link, the data being sent is encrypted for
confidentiality. Packets that are intercepted on the
shared or public network are indecipherable without the
encryption keys. The portion of the connection in which
the private data is encapsulated is known as the tunnel.
The portion of the connection in which the private data is
encrypted is known as the virtual private network (VPN)
connection.
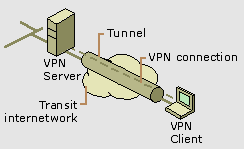 |
|
Figure 1: Virtual
private network connection |
VPN connections allow users
working at home or on the road to connect in a secure
fashion to a remote organization server using the routing
infrastructure provided by a public internetwork (such as
the Internet). From the user�s perspective, the VPN
connection is a point-to-point connection between the
user�s computer and an organization server. The nature of
the intermediate internetwork is irrelevant to the user
because it appears as if the data is being sent over a
dedicated private link.
VPN technology also allows a corporation to connect to
branch offices or to other companies over a public
internetwork (such as the Internet), while maintaining
secure communications. The VPN connection across the
Internet logically operates as a wide area network (WAN)
link between the sites.
In both of these cases, the secure connection across the
internetwork appears to the user as a private network
communication�despite the fact that this communication
occurs over a public internetwork�hence, the name virtual
private network.
VPN technology is designed to address issues surrounding
the current business trend toward increased telecommuting
and widely distributed global operations, where workers
must be able to connect to central resources and must be
able to communicate with one another.
To provide employees with the ability to connect to
organization computing resources, regardless of their
location, a corporation must deploy a scalable remote
access solution. Typically, corporations choose either a
department solution, where an internal information systems
department is charged with buying, installing, and
maintaining organization modem pools and a private network
infrastructure; or they choose a value-added network (VAN)
solution, where they pay an outsourced company to buy,
install, and maintain modem pools and a telecommunication
infrastructure.
Neither of these solutions provides the necessary
scalability, in terms of cost, flexible administration,
and demand for connections. Therefore, it makes sense to
replace the modem pools and private network infrastructure
with a less expensive solution based on Internet
technology so that the business can focus on its core
competencies. With an Internet solution, a few Internet
connections through Internet service providers (ISPs) and
VPN server computers can serve the remote networking needs
of hundreds or thousands of remote clients and branch
offices.
Common Uses of VPNs
The next few sections describe the more common VPN
configurations in more detail.
Remote Access Over the Internet
VPNs provide remote access to organization resources over
the public Internet, while maintaining privacy of
information. Figure 2 shows a VPN connection used to
connect a remote access client to an organization
intranet. This is known as a remote access VPN connection.
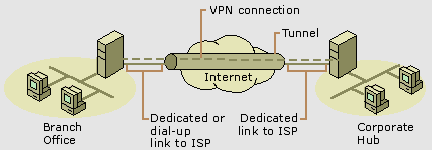
 |
|
Figure 2: Using a
VPN connection to connect a remote access client
to an organization intranet |
Rather than making a long
distance (or 1-800) call to an organization or outsourced
network access server (NAS), the user dials a local ISP.
Using the connection to the local ISP, the VPN client
creates a VPN connection between the remote access
computer and the organization VPN server across the
Internet.
Connecting Networks Over the Internet
There are two methods for using VPNs to connect local area
networks at remote sites:
� Using dedicated lines to connect a branch office to an
organization LAN.
For example, rather than using an expensive long-distance
dedicated circuit between the branch office and the
corporate hub, both the branch office and the corporate
hub routers can use a local dedicated circuit and local
ISP to connect to the Internet. The VPN software uses the
local ISP connections and the Internet to create a virtual
private network between the branch office router and
corporate hub router.
� Using a dial-up line to connect a branch office to the
Internet.
Rather than having a router at the branch office make a
long distance (or 1-800) call to a corporate or outsourced
NAS, the router at the branch office can call a local ISP.
The VPN client uses the connection to the local ISP to
create a VPN connection between the branch office router
and the corporate hub router across the Internet. This is
known as a site-to-site VPN connection.
 |
| |
|
Figure 3: Using a
VPN connection to connect two remote sites |
In both cases, the
facilities that connect the branch office and corporate
offices to the Internet are local. The corporate hub
router that acts as a VPN server must be connected to a
local ISP with a dedicated line. This VPN server must be
listening 24 hours a day for incoming VPN traffic.
Connecting Computers Over an Intranet
In some organization internetworks, the departmental data
is so sensitive that the department�s LAN is physically
disconnected from the rest of the organization
internetwork. Although this protects the department�s
confidential information, it creates information
accessibility problems for those users not physically
connected to the separate LAN.
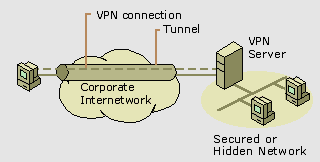 |
| |
|
Figure 4: Using a
VPN connection to connect to a secured or hidden
network |
VPNs allow the department�s
LAN to be physically connected to the organization
internetwork but separated by a VPN server. The VPN server
is not acting as a router between the organization
internetwork and the department LAN. A router would
connect the two networks, allowing everyone access to the
sensitive LAN. By using a VPN server, the network
administrator can ensure that only those users on the
organization internetwork who have appropriate credentials
(based on a need-to-know policy within the company) can
establish a VPN connection with the VPN server and gain
access to the protected resources of the department.
Additionally, all communication across the VPN can be
encrypted for data confidentiality. Those users who do not
have the proper credentials cannot view the department
LAN.
RADIUS:
The Remote Authentication Dial-in User Service (RADIUS)
protocol is a popular method for managing remote user
authentication and authorization. RADIUS is a lightweight,
UDP-based protocol. RADIUS servers can be located anywhere
on the Internet and provide authentication (including PPP
PAP, CHAP, MS-CHAP, MS-CHAP v2, and EAP) and authorization
for access servers such as NASes and VPN servers.
In addition, RADIUS servers can provide a proxy service to
forward authentication requests to distant RADIUS servers.
For example, many ISPs have agreements to allow roaming
subscribers to use local services from the nearest ISP for
dial-up access to the Internet. These roaming alliances
take advantage of the RADIUS proxy service. If an ISP
recognizes a user name as being a subscriber to a remote
network, the ISP uses a RADIUS proxy to forward the access
request to the appropriate network.
Windows Server 2003 includes a RADIUS server and proxy
with the Internet Authentication Service (IAS); an
optional Windows networking component installed using
Control Panel-Network.
NOTE:
1. The possibilities in areas using GPRS like VPN and
RADIUS technologies are abundant and have to be
discovered.
Future documents will try to keep you updated about these
trends.
2. Similarly other areas of applications will be
documented as early as possible
3. Please get back with your suggestions on this document.
|